AWS VPC Endpoints – A Quick Guide
By default if you try to access the some of the resource from another resource in AWS cloud, the traffic flows through Internet. For example, if you want to access a S3 bucket from EC2 instance, the traffic will flow through internet. Now this is not a problem for most of the organisations as traffic is encrypted but internet itself is unsecure. Some organisations due to very sensitive nature of data or huge volume of data cannot send it over internet. This is where VPC endpoints comes in picture. A VPC endpoint lets your data to flow through AWS internal Private network.
The below is the list of issues which can force you to use VPC endpoint:
- If your data is large, you will have high data usage cost.
- For high data size, you will face network latency as data is flowing through internet.
- Internet Gateway can choke due to high volume of data.
- Very sensitive nature of data can pose an issue if traffic flows through internet.
A VPC endpoint lets AWS services communicate via AWS private network without any NAT Gateway or Internet Gateway. It helps address all the issues mentioned above. A VPC endpoint is service specific, for example, to access S3 you need a S3 VPC interface endpoint or VPC Gateway endpoint.
Types of VPC endpoints
- Gateway Endpoints
- Interface Endpoints
- VPC Endpoint Service
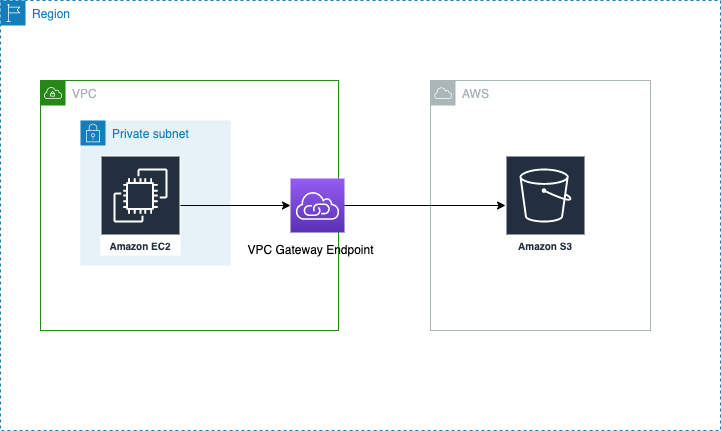
VPC Gateway Endpoint
When you create a VPC gateway endpoint, it serves as a target for your route table associated with your subnet. So it is something you add to your route table as target just like you do for NAT gateway or Internet Gateway.

Above is an example of S3 VPC Gateway endpoint. So like mentioned above Target of route table is set as VPC gateway endpoint.
The destination pl prefix is Amazon managed prefix list corresponding to S3 service CIDRs. When you create a VPC Gateway endpoint, you can select route table and this rule gets added to your route table. If manually adding you can get prefix list from managed prefix lists under VPC page.
Once it is added, now your traffic is flowing through AWS private network.
Some downsides of using VPC Gateway Endpoint:
- VPC Gateway Endpoint is not part of your VPC and is hosted by AWS in AWS managed space, so makes it difficult to use from VPN or Direct Connect.
- VPC Gateway Endpoints are supported within same region.
- Only IPv4 traffic is supported.
- You must turn on DNS resolution in VPC. If using your own DNS servers instead of default AWS, you must ensure requests resolve to IPs maintained by AWS.
- Only supports S3 and Dynamodb for now.
Interface Endpoints
An interface endpoint is basically an Elastic Network Interface (ENI) with private IP from IP range of your subnet. It is an entrypoint for traffic to a supported AWS service.
It has following benefits over VPC Gateway Endpoints.
- Let us use Security Groups and policy based control. So can control the access and incoming traffic.
- Since IP is from our custom VPC, hence it is supported by VPN and Direct Connect.
- Interface Endpoint supports a lot of services.
An interface endpoint can be associated with all public and private subnets. Then you can control access level (for example, which bucket can be accessed and what kind of actions can be performed)and incoming traffic (what CIDRs or SG allowed) using policy and Security Groups.
You can access services within same region the Interface Endpoint is created. For example, yuu can access S3 buckets of us-east-1 region only if your interface endpoint is created in us-east-1 region. But you can be in any region to use Interface endpoint. You always need to mention region of Interface Endpoint while calling a service.
aws s3 ls --region us-east-1Just like VPC Gateway endpoint, if your private subnet do not have NAT Gateway, then you can still access AWS services using AWS private network with help of Interface Endpoint.
VPC Endpoint Services
For SAAS services like Datadog or New Relic, we need to upload metrics via Internet. Since metrics are sensitive some organisations need this to be sent over private network.
Since most of these services are hosted in AWS, we could do this by collaborating with these service providers . One solution can be VPC peering, but it wont work as VPC CIDRs of many customers will be same.
So to resolve this AWS provides VPC endpoint services.
In this set up, service providers register their services in their VPC through a NLB (Network Load Balancer) or Gateway Load Balancer and then in customer VPC, customer creates a VPC Endpoint Service at their end which connects to this NLB or Gateway LB.
Conclusion
So we did a quick overview of VPC endpoints in this blog. We learnt different types and how they can be useful to us.